On April 12th, Palo Alto Networks released a CVE advisory for CVE-2024-3400, a critical vulnerability identified in the GlobalProtect Gateway feature of PAN-OS, the operating system for Palo Alto Networks firewalls. This command injection vulnerability allows unauthenticated attackers to execute arbitrary commands with root privileges on the affected devices. Due to the low attack complexity requirements and lack of initial privileges required, a CVSS score of 10/10 has been assigned reflecting its the highest level of severity and its potential impact.
This vulnerability specifically affects PAN-OS versions 10.2, 11.0, and 11.1 when both the GlobalProtect gateway and device telemetry features are enabled. Fixes for these versions are in development and are estimated to be released on April 14th, 2024. Cloud NGFW, Panorama appliances, and Prisma Access are not impacted by this vulnerability. All other versions of PAN-OS are also not impacted.
Immediate actions recommended by Palo Alto Networks include applying a Threat Prevention update with Threat ID 95187, which blocks the attack vectors for this vulnerability. Users are urged to monitor and apply forthcoming patches scheduled for release by April 14, 2024, to fully address the vulnerability in PAN-OS versions 10.2.9-h1, 11.0.4-h1, and 11.1.2-h3. Until these patches are applied, customers are advised to disable device telemetry if it is not critical to their operations.
Palo Alto Networks and CISA have confirmed limited but active exploitation in the wild with multiple POC Exploits scripts becoming publicly available on April 12th.
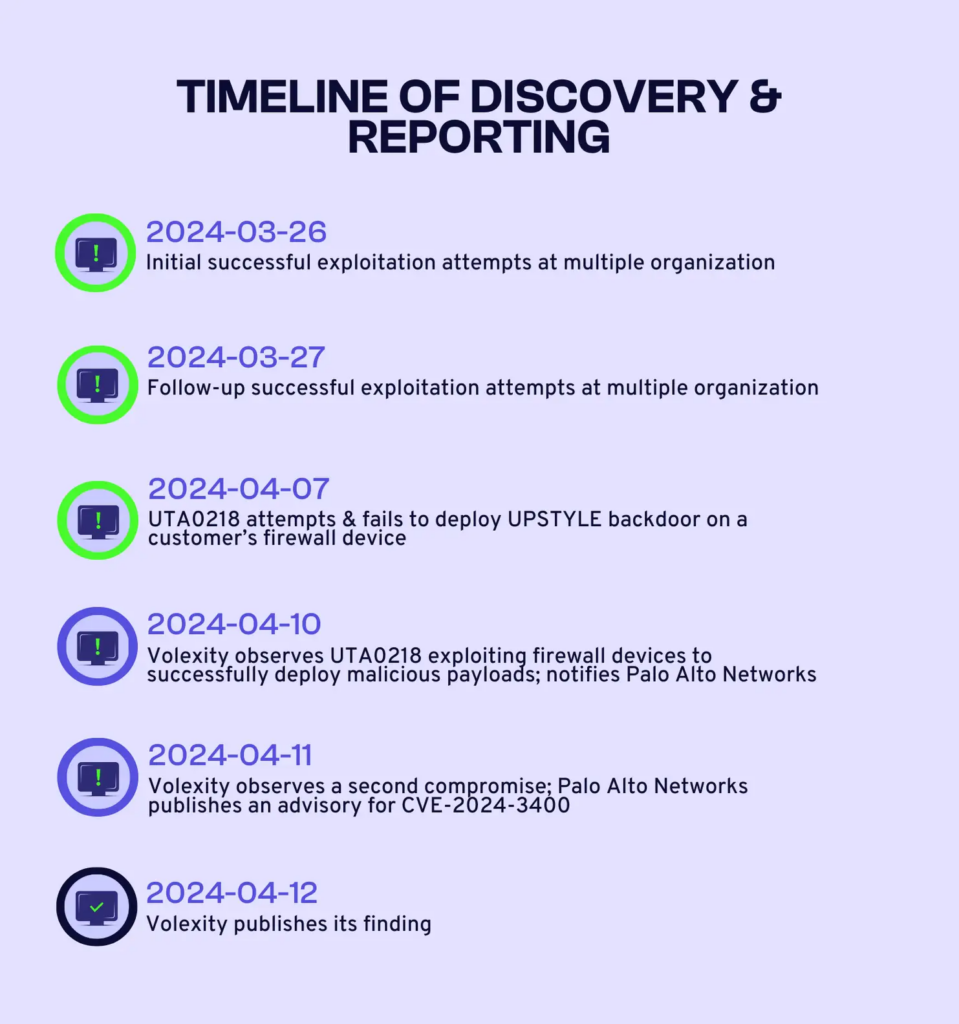
Volexity, as detailed in their blog post, first identified zero-day exploitation of CVE-2024-3400 on April 10th, 2024 executed by the threat actor UTA0218 which was able to remotely exploit a Palo Alto Firewall, create a reverse shell, and move laterally across the environment. Volexity’s investigation further revealed successful exploitation of this vulnerability by UTA0218 across multiple organizations dating back to March 26th, 2024.
Volexity notes that “The tradecraft and speed employed by the attacker (UTA0218) suggests a highly capable threat actor with a clear playbook of what to access to further their objectives.” Based on their analysis, Volexity “assesses that it is highly likely UTA0218 is a state-backed threat actor based on the resources required to develop and exploit a vulnerability of this nature, the type of victims targeted by this actor, and the capabilities displayed to install the Python backdoor and further access victim networks.”
Nessus has released detection for CVE-2024-3400 via Nessus Plugin ID 193255.
The discovery of CVE-2024-3400 shows that threat actors are continuing to target edge devices and underscores the importance of rigorous network security practices, including monitoring of network defense mechanisms to protect against potential unauthorized access and system compromises, and vulnerability management through active scans.
The CleanINTERNET solution continues to utilize threat intelligence to protect against the stages of the attackers kill chain from Reconnaissance and identification of vulnerable targets, to Delivery and establishing persistence, and Command and Control. Centripetal expects a sharp increase in observed Cyber Threat Intelligence indicators related to the exploitation of CVE-2024-3400 in the coming days as threat actors race to exploit this vulnerability before the window of opportunity to do so closes.
If you are currently running one of the affected versions of PAN-OS, please contact support@centripetal.ai.
Centripetal is pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
