Malware Details
The origin of the word “Rhadamanthys”, goes back to Greek mythology where he was a legendary figure who ruled as king of Crete. Born to Zeus and Europa, he held the status of demigod and was renowned for his wisdom.
Rhadamanthys Stealer is a sophisticated information stealer written in C++ that employs multiple evasion techniques. The malware utilizes a custom packer for code obfuscation and incorporates anti-VM and anti-debugging mechanisms to prevent analysis. It has likely been part-written or coded with LLM assistance due to artifacts observed within Powershell code according to ProofPoint research. For its command and control communication, it establishes connections through HTTP POST requests to its C2 infrastructure.
Initial access tactics to disseminate include, but are not limited to, using GoogleAds to distributed fake websites imitating legitimate software platforms like AnyDesk, Zoom, Microsoft Teams and Notepad++. It is often bundled with the authentic software to reduce user suspicion, with these deceptive sites promoted via Google ads that outrank legitimate search results.
The malware’s primary function is comprehensive data exfiltration. It systematically harvests credentials stored in web browsers, extracts cryptocurrency wallet data, and captures system information including screenshots. The stealer specifically targets authentication tokens, cookies, and stored passwords from multiple browsers. Additionally, it has functionality to compromise password manager data and collect credentials from FTP clients installed on the infected system. The malware maintains persistence through its robust C2 communication channel while actively evading detection mechanisms.
Rhadamanthys Stealer is operated as a Malware-as-a-Service (MaaS) model, where cybercriminals can purchase subscriptions to use the malware through underground marketplaces. However, a key differentiator of what could be commodity malware, is the service model offered by the threat actor which includes regular updates, technical support, and a web panel for managing infected systems, making it accessible to threat actors with varying levels of technical expertise. Rhadamanthys Stealer v0.9 was observed, by X user, @g0njxa, to still be online as of February 10, 2025 with it’s first update of 2025 adding features like an increased collection capacity for browser extensions and additional persistence framework to support auto-start and long-term system residency.
Centripetal’s View
In the past month, the CleanINTERNET® service observed outbound web traffic events to microsoft.teams-live[.]com [BDN] 82.221.136[.]26. The trigger domain was observed to use a traffic distribution system (TDS) to direct victims to various landing pages dependent on their browser values, amongst which was an alleged Microsoft Teams download page. It was observed that the victim device downloaded “application_setup[.]exe”(URLScan) which contained what is suspected by open-source intelligence threads to be malicious payloads for Cobalt Strike and Rhadamanthys Stealer.
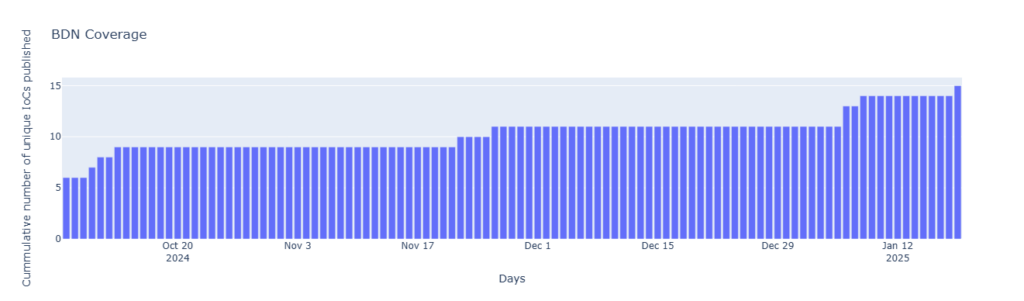
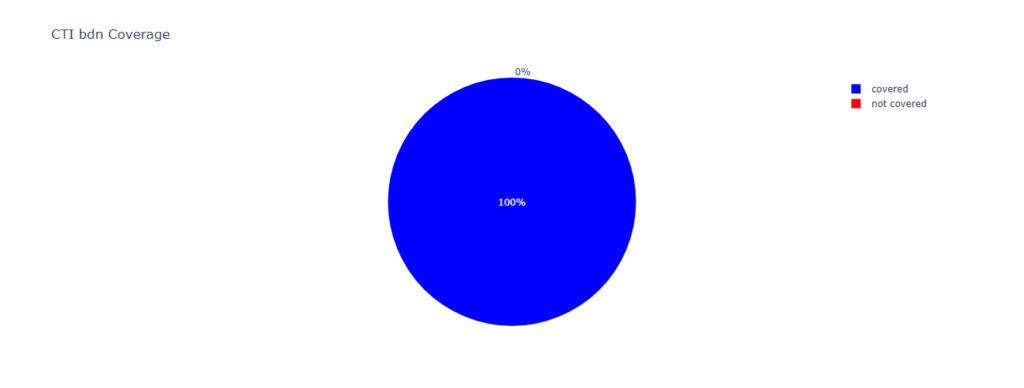
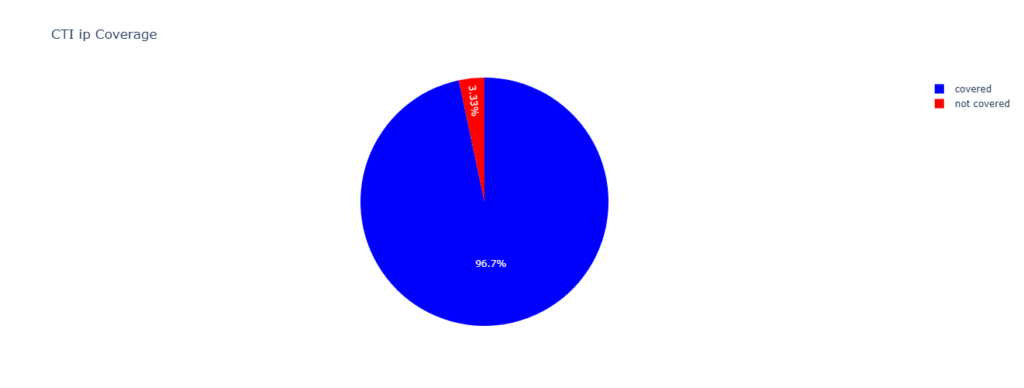
When reviewing what coverage Centripetal offered its customers on this specific campaign, a general enhanced IOC coverage is expected as time passes. This behavior is generally expected as IOCs are identified and enter CTI blocking. In this specific campaign, complete BDN coverage of observed and attributed IOCs has been achieved by threat intelligence providers. By the time the Rhadamanthys IOCs were observed in customers environments, Centripetal had a complete BDN coverage and a high percentile of coverage observed on the cited IPs.
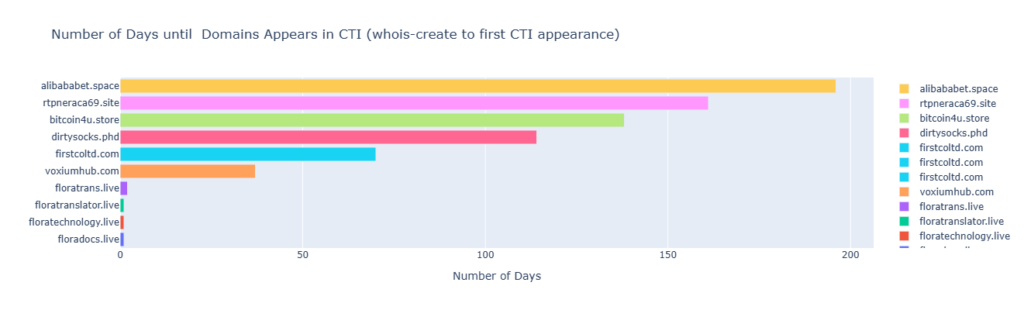
The below figure shows the domains that had the longest durations of being undetected from their initial creation to their first appearance in CTI. It is surprising to see the top four offending domains are generic Top Level Domains (gTLD) with .space, .site, .store and .phd. The flora [random dictionary word] .live domains have multiple attributes that would suspect them to be dictionary domain generated algorithms (DDGAs) and as such entered into CTI quickly after their creation. Given historically threat actors frequently leveraged DDGAs and DGAs maliciously, this is not an unexpected result.
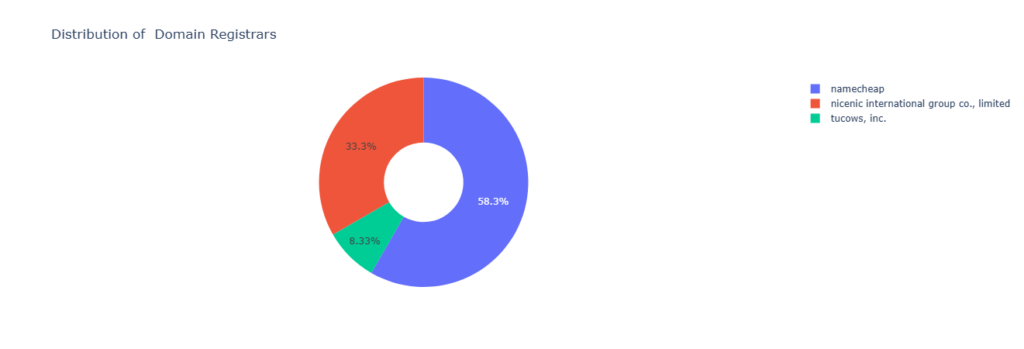
To dig into the domains a little further, the distribution of their registrars are relatively small. The Top offender of the registered domains is NameCheap, a reputable registrar option that is used extensively both legitimately and abused by threat actors due to its affordability and accessibility.
Due to their popularity with threat actors, both NameCheap and NiceNIC are featured in the list of top three domain Registrars by Phishing domains as published by the Cybercrime Information Center – a repository for studies, measurements, data sets, statistics, and analyses of global security threats in their latest assessment from August to October 2024 (source: CCIC). Unsurprisingly, 91% of the campaign related domains were registered with these two registrars. With 8% of campaign related domains, Tucows was found to be 13th on the CCIC Phishing Domains List.
Historically, the malware author usually did not discriminate in who the malware was distributed to – only to remark in one of its earliest releases: “as long as the target is not located in the commonwealth of independent states”. From the analysis of the CleanINTERNET customer base, the IOCs most frequently hit in the education and healthcare industry, which would align with demographic targeted with advertising campaigns which masqueraded the payloads in “legitimate” and well-known tools like NotePad++, Teamviewer and, as observed in our customer’s environment, Microsoft Teams.
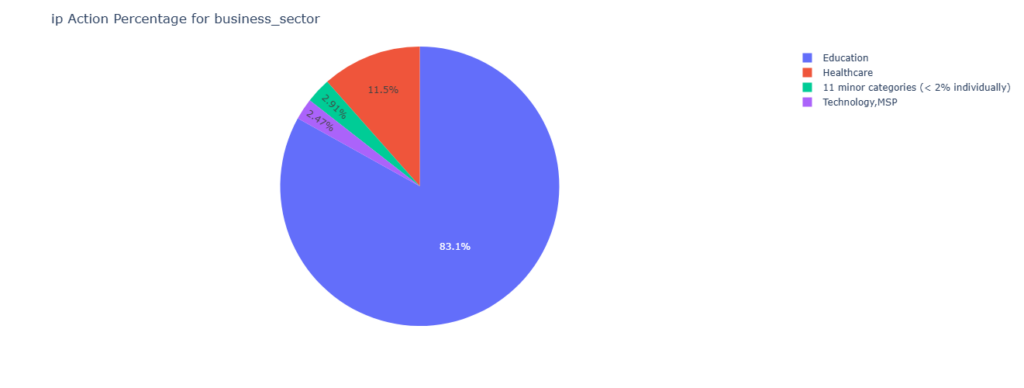
As Rhadamanthys evolved its sophisticated MaaS model with ever transient techniques and tactics in its dissemination dependent on the buyer, its IOCs continue to be identified and mitigated in a timely manner by the threat intelligence community. However, it is important to note that complete IOC coverage was not observed by a single threat intelligence provider alone. The consolidation of CTI into a multi-faceted defense was the key to providing solid IOC coverage against this threat.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- https://malpedia.caad.fkie.fraunhofer.de/details/win.rhadamanthys
- https://research.checkpoint.com/2024/massive-phishing-campaign-deploys-latest-rhadamanthys-version/
- https://any.run/report/39f66690aae07bf9f1f4a5470409f187aff4eb3cd4a1a9ce6b76e88c263a5adb/724715d3-1ecd-4688-8358-5e62c9ddf8e5
- https://x.com/CyberRaiju/status/1882196339569901893
- https://threatfox.abuse.ch/ioc/1392440/
- https://cybersecuritynews.com/fake-microsoft-teams-page-drops-malware-on-windows/
- https://github.com/PaloAltoNetworks/Unit42-timely-threat-intel/blob/main/2025-01-22-IOCs-for-malware-from-fake-Microsoft-Teams-site.txt
- https://urlscan.io/result/646d87f8-c862-44e8-a995-3551d32a69d5/#summary
- https://urlscan.io/result/c1fb78d5-be17-4c7d-b949-26f86ab45a93/
- https://x.com/g0njxa/status/1888978231249801323
- https://static1.squarespace.com/static/63dbf2b9075aa2535887e365/t/66cde404c8345e766972319c/1724769286084/PhishingLandscape2024.pdf
- https://blog.talosintelligence.com/suspected-coralraider-continues-to-expand-victimology-using-three-information-stealers/
- https://outpost24.com/blog/rhadamanthys-malware-analysis/
- https://research.checkpoint.com/2023/rhadamanthys-the-everything-bagel-infostealer/
- https://cofense.com/blog/new-maas-infostealer-malware-campaign-targeting-oil-gas-sector/
Repos with IOCs