On March 4, 2025, Broadcom, which acquired VMware in 2023, released security updates to fix three actively exploited vulnerabilities in VMware ESXi, Workstation, and Fusion that could result in code execution and information disclosure. CVE-2025-22224 is a critical TOCTOU (Time-of-Check Time-of-Use) race condition vulnerability that leads to an out-of-bounds write, allowing an attacker with administrative privileges on a virtual machine to execute code as the VMX process on the host. CVE-2025-22225 is a high-severity arbitrary write vulnerability that enables an attacker with VMX process privileges to perform kernel writes, potentially leading to a sandbox escape and host compromise. CVE-2025-22226 is a high-severity out-of-bounds read flaw in the Host Guest File System (HGFS), which could allow attackers with administrative VM privileges to access sensitive memory from the VMX process. Broadcom noted that exploitation requires elevated privileges, indicating these vulnerabilities have likely been used in targeted attacks where threat actors first gained initial access to victim systems before moving laterally into the hypervisor.
Impacted Products and Versions
| Affected Products | CVEs | |
| VMware ESXi | CVE-2025-22224, CVE-2025-22225, CVE-2025-22226 | 8.0 before ESXi80U3d-24585383 8.0 before ESXi80U2d-24585300 7.0 before ESXi70U3s-24585291 |
| VMware Workstation | CVE-2025-22224, CVE-2025-22226 | 17.x before 17.6.3 |
| VMware Fusion | CVE-2025-22226 | 13.x before 13.6.3 |
| VMware Cloud Foundation | CVE-2025-22224, CVE-2025-22225, CVE-2025-22226 | 5.x, 4.5.x |
| VMware Telco Cloud Platform | CVE-2025-22224, CVE-2025-22225, CVE-2025-22226 | 5.x, 4.x, 3.x, 2.x |
| VMware Telco Cloud Infrastructure | CVE-2025-22224, CVE-2025-22225, CVE-2025-22226 | 3.x, 2.x |
VMware ESXi and Workstation TOCTOU Race Condition Vulnerability [CVE-2025-22224]
CVE-2025-22224 is a critical-severity TOCTOU (Time-of-Check Time-of-Use) vulnerability affecting VMware ESXi, Workstation and other products. This flaw arises from a TOCTOU race condition, leading to an out-of-bounds write. An attacker with local administrative privileges on a virtual machine can exploit this vulnerability to execute code as the VM’s VMX process running on the host.
Vulnerability Type (CWE)
CWE-367: Time-of-check Time-of-use (TOCTOU) Race Condition
CVSS Score
9.3 (Critical)
Exploit Process
- Gaining Local Administrative Privileges: an attacker must first obtain administrative privileges on the guest VM. This could be achieved through various means, such as exploiting other vulnerabilities or leveraging existing access rights.
- Exploiting the TOCTOU Race Condition: with administrative privileges, the attacker can exploit the TOCTOU race condition within the VMCI component. The condition involves the product checking the state of a resource before using that resource, but the resource’s state can change between the check and the use in a way that invalidates the results of the check. This can cause the product to perform invalid actions when the resource is in an unexpected state. This weakness can be security-relevant when an attacker can manipulate the timing between the check of a condition and the use of the result, leading to an out-of-bounds write.
- Executing Code as the VMX Process: the out-of-bounds write allows the attacker to execute arbitrary code as the VMX process on the host, potentially leading to a full compromise of the host system. VMX is a process that runs in the VMkernel that is responsible for handling input/output to devices that are not critical to performance.
Watch out for:
- Unusual or unexpected write operations by the VMCI component.
- Access logs indicating attempts to exploit race conditions within the VMCI component.
VMware ESXi Arbitrary Write Vulnerability [CVE-2025-22225]
CVE-2025-22225 is high-severity arbitrary write vulnerability affecting VMware ESXi and other products. This weakness allows a malicious actor with privileges within the VMX process to perform arbitrary kernel writes, potentially leading to a sandbox escape and further compromising the host system.
Vulnerability Type (CWE)
CWE-123: Write-what-where Condition
CVSS Score
8.2 (High)
Exploit Process
- Gaining Privileges within the VMX Process: an attacker must first obtain privileges within the VMX process. This could be achieved through various means, such as exploiting other vulnerabilities or leveraging existing access rights.
- Crafting Malicious Payloads: with the acquired privileges, the attacker crafts specific payloads designed to perform arbitrary kernel writes. These payloads are meticulously constructed to target critical memory regions within the host’s kernel.
- Executing Arbitrary Kernel Writes: the malicious payloads are executed, triggering the arbitrary write operations. By writing to specific kernel addresses, the attacker can manipulate the host’s operating system behavior.
- Achieving Sandbox Escape: through these arbitrary writes, the attacker can modify kernel structures or inject malicious code, effectively escaping the sandbox environment. This allows the attacker to execute code with elevated privileges on the host system, leading to potential full system compromise.
Watch out for:
- Unusual access patterns or logs indicating attempts to write to kernel memory regions.
- Detection of tools or scripts designed to exploit arbitrary write vulnerabilities in VMware environments.
VMware ESXi, Workstation, and Fusion Information Disclosure Vulnerability [CVE-2025-22226]
CVE-2025-22226 is a high severity information disclosure vulnerability affecting VMware, EXSi, Workstation and other products. This vulnerability arises from an out-of-bounds read in the Host Guest File System (HGFS), potentially allowing attackers with administrative privileges on a virtual machine (VM) to access sensitive memory from the VMX process.
Vulnerability Type (CWE)
CWE-125: Out-of-bounds Read
CVSS Score
7.1 (High)
Exploit Process
- Crafting Malicious Requests: the attacker crafts specific requests that interact with the HGFS component, aiming to trigger the out-of-bounds read condition.
- Triggering the Vulnerability: by executing these crafted requests within the guest VM, the attacker induces the HGFS to perform read operations beyond its allocated memory boundaries.
- Accessing VMX Process Memory: this out-of-bounds read allows the attacker to access portions of the VMX process memory, potentially leaking sensitive information from the host system.
Watch out for:
- Unusual access patterns or logs indicating attempts to read from the VMX process memory.
- Detection of tools or scripts designed to exploit out-of-bounds read vulnerabilities in VMware environments.
Interaction with Other Vulnerabilities:
While CVE-2025-22226 primarily concerns information disclosure, CVE-2025-22225 focuses on arbitrary kernel writes leading to sandbox escape, and CVE-2025-22224 primarily concerns code execution through a race condition, they could be leveraged in conjunction with one another to facilitate more severe attacks, such as privilege escalation or arbitrary code execution on the host system.
Exploitation is the Wild
Microsoft has identified exploitation of CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226 in the wild and reported the findings to VMware. This confirms that attackers have actively used these vulnerabilities to compromise systems before public disclosure. The existence of these exploits in real-world attacks significantly increases the urgency of patching affected VMware environments.
Additionally, in the weeks before VMware disclosed the vulnerabilities, a VM escape exploit was being advertised on an underground forum for $150,000. The impacted versions listed in the forum post overlap with the versions now confirmed as vulnerable, suggesting a possible connection. However, it remains unclear whether the exploit for sale is the same one discovered in the wild by Microsoft.
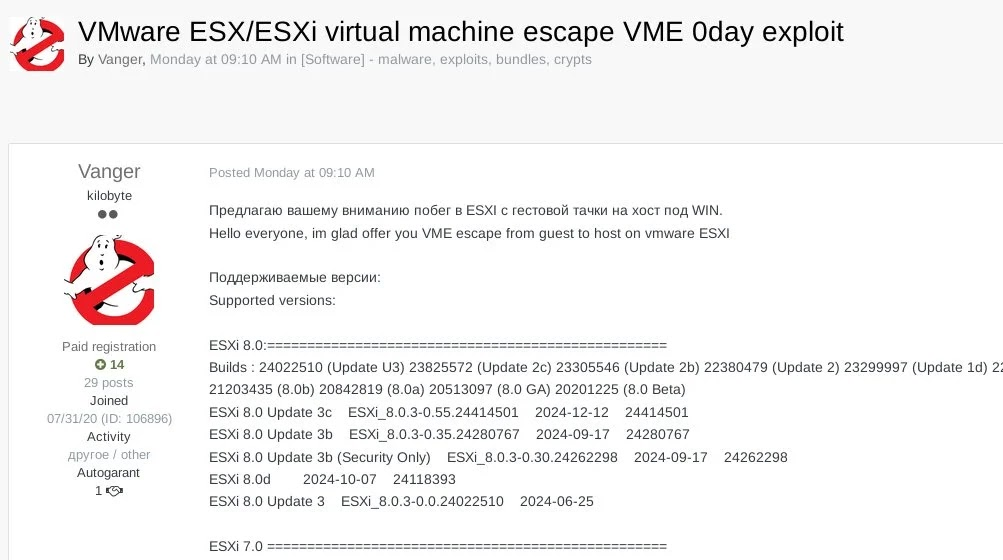
At present, the exploit has not been publicly leaked, meaning it is not available on platforms like GitHub, nor has anyone released a detailed reverse-engineering write-up from VMware’s patch. This provides organizations with a critical but limited window to apply patches before more threat actors gain access to a working exploit.
If a full exploit chain is released publicly—whether through leaked proof-of-concept code or a technical breakdown—widespread adoption by threat actors is inevitable. This would enable attackers to escalate low-privileged access within an organization to full control over virtualized environments, potentially affecting multiple organizations running vulnerable VMware deployments. Security teams must act immediately to apply patches and monitor for signs of compromise.
Mitigation Steps
- Identify Affected Systems: determine which systems are running the impacted versions of VMware ESXi, Workstation, Fusion, and related products.
- Apply Patches Promptly: download and install the appropriate patches from VMware’s official channels.
- Review Security Configurations: ensure that only authorized personnel have administrative privileges on virtual machines, limiting potential attack vectors.
- Implement Network Segmentation: isolate virtualized environments and management interfaces from general network traffic to limit an attacker’s ability to move laterally and exploit vulnerabilities across multiple systems.
Centripetal’s Perspective
Centripetal’s CleanINTERNET® service provides a proactive, intelligence-driven defense against critical vulnerabilities like CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226, which impact VMware ESXi, Workstation, Fusion, and related products. These vulnerabilities allow attackers with local administrative privileges on a virtual machine to execute code as the VMX process, perform arbitrary kernel writes leading to sandbox escapes, or access sensitive memory from the VMX process, potentially compromising the host system.
Leveraging billions of threat indicators, CleanINTERNET® dynamically blocks malicious traffic using real-time global threat feeds and augmented human analysis, proactively protecting organizations from exploitation attempts involving known IoCs. By reducing the attack surface, enhancing security operations, and ensuring business continuity, CleanINTERNET® enables organizations to adopt a proactive and adaptive cybersecurity strategy against evolving threats.
The vulnerabilities CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226 pose significant security risks to VMware ESXi, Workstation, Fusion, and related products, particularly when chained together to achieve full system compromise. Exploiting these vulnerabilities requires existing privileged access, meaning an attacker must first compromise a virtual machine before escalating privileges to the hypervisor level. However, these vulnerabilities can be chained together to maximize impact, allowing an attacker to move from a compromised VM to full control over the underlying ESXi host. According to Rapid7’s analysis, this escalation path makes them particularly dangerous in targeted attacks, where threat actors with initial footholds in a virtualized environment could achieve full system takeover.
VMware has released security patches and strongly urges immediate updates to mitigate these vulnerabilities. Organizations should apply patches promptly to affected VMware products, restrict administrative privileges on virtual machines to limit an attacker’s ability to exploit these vulnerabilities, and monitor for indicators of compromise, including unusual VMCI activity, attempts to write to kernel memory, or unauthorized access to the VMX process memory. Implementing network segmentation is also crucial to limit an attacker’s ability to move laterally within the environment.
If you are a current client of VMware ESXi, Workstation or Fusion please contact support@centripetal.ai .
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- https://www.cve.org/CVERecord?id=CVE-2025-22224
- https://cwe.mitre.org/data/definitions/367.html
- https://www.cve.org/CVERecord?id=CVE-2025-22225
- https://cwe.mitre.org/data/definitions/123.html
- https://www.cve.org/CVERecord?id=CVE-2025-22226
- https://cwe.mitre.org/data/definitions/125.html
- https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/25390
- https://www.infosecurity-magazine.com/news/vmware-patch-exploited-zero-day/
- https://www.securityweek.com/broadcom-patches-3-vmware-zero-days-exploited-in-the-wild/
- https://thehackernews.com/2025/03/vmware-security-flaws-exploited-in.html
- https://cybersecuritynews.com/threat-actor-vmware-esxi-0-day/
- https://doublepulsar.com/use-one-virtual-machine-to-own-them-all-active-exploitation-of-esxicape-0091ccc5bdfc
- https://www.rapid7.com/blog/post/2025/03/04/etr-multiple-zero-day-vulnerabilities-in-broadcom-vmware-esxi-and-other-products/
- https://github.com/vmware/vcf-security-and-compliance-guidelines/tree/main/security-advisories/vmsa-2025-0004
