CVE-2025-24859 is a critical security vulnerability in Apache Roller, a Java-based web application used for blogging and content management, that allows unauthorized session reuse due to insufficient session expiration after a user’s password is changed. Notably, the application fails to invalidate active user sessions upon password modification, irrespective of whether the change is initiated by the user or an administrative entity. When users update their credentials, previously established sessions remain valid, allowing attackers in possession of active session tokens to continue accessing the system without re-authentication. The issue affects Apache Roller prior to v6.1.5. and has been assigned a CVSS score of 10.0 (Critical), reflecting its high impact on confidentiality, integrity, and availability. The exploitation of this flaw exposes systems to unauthorized data access, privilege escalation, and persistence threats, especially in scenarios where session tokens are leaked or stolen. (The Hacker News, 2025)
Vulnerability Type (CWE)
CWE-163: Insufficient Session Expiration
This vulnerability arises when a web site or application permits an attacker to reuse old session credentials or session IDs for authorization.
CVSS Score
Base Score: 10.0 (Critical)
Attack Vector: Network (AV:N)
Attack Complexity: Low (AC:L)
Privileges Required: None (PR:N)
User Interaction: None (UI:N)
Scope: Unchanged (S:U)
Impact on CIA: High
- Confidentiality: High (SC:H)
- Integrity: High (SI:H)
- Availability: High (SA:H)
Impacted Versions
| Version | Status |
|---|---|
| 6.1.4 or prior | Vulnerable |
| 6.1.5 or later | Patched |
Mitigation Steps
- Upgrade immediately to Apache Roller 6.1.5 or later, where session invalidation is enforced post-password change.
- Review session management settings to ensure best practices are applied, including timeouts and single-session constraints.
- Monitor for unusual session activity, especially logins from unfamiliar IPs after password resets.
- Educate users to report unexpected account activity.
Exploit Process
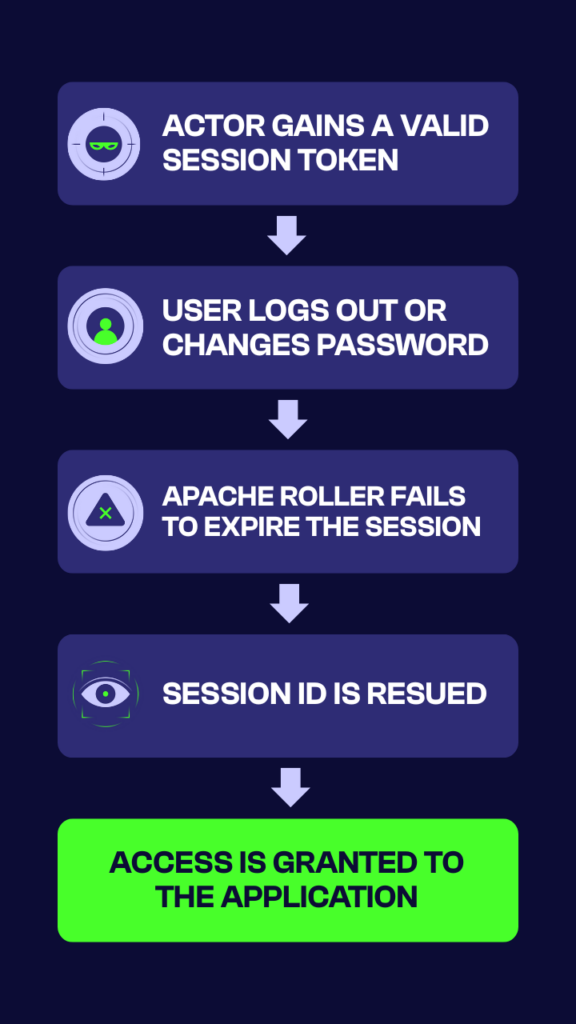
- Attacker gains a valid session token:
- Through XSS injection, packet sniffing (Man-in-the-Middle attacks), or by exploiting predictable session ID generation (e.g., weak entropy in JSESSIONID).
- In some cases, attackers may exploit insufficient HTTPS enforcement to intercept tokens over unencrypted channels.
- User logs out or changes password:
- The user assumes their session has been terminated or invalidated across all devices.
- Apache Roller fails to expire the session:
- The application does not invalidate the existing session token after logout or password change.
- Attacker reuses the session ID:
- The attacker sends HTTP requests with the stolen JSESSIONID cookie.
- Roller incorrectly accepts and processes the session token, restoring full authenticated access.
- Attacker accesses the application:
- The attacker can potentially escalate privileges or exfiltrate sensitive information.
- This persists until the server is restarted or the session is manually revoked.
Timeline
- April 9, 2025 – Announcement for release of patched v6.1.5.
- April 11, 2025 – Vulnerability reported by security researcher Haining Meng, who is credited for identifying this critical flaw.
TTPs
- Session Hijacking via XSS or MITM: Leveraging client-side vulnerabilities or insecure transport to intercept session tokens.
- Abuse of Long-Lived Sessions: Exploiting Roller’s failure to terminate sessions post-password change or logout.
- Token Replay: Re-sending valid session cookies (JSESSIONID) to maintain access.
- Avoidance of Authentication Logs: Reuse of existing sessions avoids triggering new login events.
- Persistence via Passive Listening: Attackers may lie dormant until sessions naturally expire or are forcibly cleared.
IOCs
- Continued session activity from outdated credentials.
- Multiple geographic IPs using the same session ID.
- Absence of login events after a password change.
- Session tokens active for abnormal durations (e.g., days/weeks).
- Access patterns inconsistent with legitimate user behavior.
CVE-2025-24859 represents a critical session management flaw in Apache Roller, enabling attackers to retain access using old session tokens even after a user changes their password. This exposes systems to unauthorized access, persistent intrusion, and potential lateral movement within an environment. With a CVSS score of 10.0, the vulnerability demands immediate attention. Organizations should upgrade to Roller v6.1.5 or later, implement strict session invalidation policies, and monitor session activity for anomalies. Proactive threat detection and session lifecycle management are essential to mitigate risks from this exploit. (Cyber News, 2025).
Centripetal’s Perspective
Centripetal’s CleanINTERNET® service provides a proactive, intelligence-driven defense against vulnerabilities like CVE-2025-24859, which allows continued access to the Apache Roller application through old sessions even after password changes, potentially enabling unauthorized access if credentials were compromised. Leveraging billions of threat indicators, CleanINTERNET dynamically blocks malicious traffic using real-time global threat feeds and augmented human analysis, proactively protecting organizations from exploitation attempts involving known IoCs. This approach ensures reduced attack surface, enhanced security operations, and uninterrupted business continuity, enabling organizations to adopt a proactive and adaptive cybersecurity strategy against evolving threats.
If you currently use Apache Roller please contact support@centripetal.ai.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- The Hacker News – Critical Apache Roller Vulnerability (CVSS 10.0) Enables Unauthorized Session Persistence
- National Vulnerability Database – CVE-2025-24859 Detail
- Cyber News – Apache Roller Flaw Exposes Systems to Unauthorized Access
- Apache Roller Threads – CVE-2025-24859: Apache Roller: Insufficient Session Expiration on Password Change
- Apache Roller Threads – Apache Roller 6.1.5 is available for download
- Medium – CVSS 10.0: Critical Apache Roller Vulnerability Enables Unauthorized Session Persistence
- DarkReading – Max Severity Bug in Apache Roller Enabled Persistent Access
