PowerSchool, a widely used cloud-based and on-premises platform, experienced a data breach reported on December 28, 2024. The platform helps K-12 schools manage student and teacher information, including Personally Identifiable Information (PII), attendance records, grades, medical information, and Social Security numbers. The breach affected both cloud and on-premises customers after a compromise of maintenance account credentials allowed the threat actor to exfiltrate sensitive data. The exact scope of the data compromised is still being investigated, but it is believed that many schools and districts were affected. PowerSchool’s response to the breach included notifying law enforcement, securing the compromised account, engaging with affected schools, and collaborating with cybersecurity firms CrowdStrike and CyberSteward to investigate the incident.
Breach Details
- Affected platform: PowerSource, used for customer support
- Compromised account: Maintenance user with UID=200A0
- Affected customers: Cloud and on-premises deployments of PowerSchool. The exact number is still unknown; a final report with more accurate information will be available on January 17, 2025
Compromise
An unidentified threat actor compromised a PowerSchool maintenance PowerSource account and gained access to school databases containing student and teacher records with personal information. The attacker exported this data to a CSV file. PowerSchool discovered the breach on December 28, 2024. Although reconnaissance activities may have occurred earlier, system logs indicate that data compromise began on December 20, 2024. (DataBreaches, 2025)
Indicators of Compromise (IOCs)
Ukrainian IP address
- Data exfiltration was first seen to IP address 91.218.50[.]11 registered in Ukraine to Virtual Systems LLC.
Assessment
System administrators are encouraged to follow these instructions for verifying and auditing logs to determine whether unauthorized data exfiltration occurred. A document authored by Romy Backus, a Student Information Specialist (SIS) at the American School of Dubai, has been made available for public viewing. (Backus, 2025)
The steps are outlined as follows:
Part 1
Access to ps-log-audit from system management provides logged information that can help identify any unauthorized data exports.
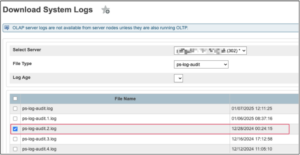
Part 2
Three things to look for:
- UID=200A0 (Compromised maintenance account)
- Exported files: Students_export.csv / Teachers_export.csv
- Export record ID (EX): Identifies the fields extracted during each export

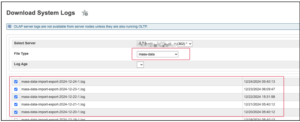
Part 3
The Export ID (EX) helps identify the exact fields that were exported. Once mass-data logs (Figure 3) are downloaded from the system management, an EX-match should reveal all fields included in each export. (Figure4)

Vendor Response
PowerSchool has announced that it will proactively communicate with affected school districts, providing a guidance package that includes outreach emails, talking points, and FAQs to help inform affected families and educators (BleepingComputer, n.d.).
PowerSchool will also offer:
- Credit monitoring for affected adults involved in the compromise
- Identity protection services for minors
A final report with more details will be available on January 17, 2025.
If you are a current client of PowerSchool please contact support@centripetal.ai. Centripetal is able to offer assistance with the audit of PowerSchool Logs or Network Logs to check for unauthorized access upon request.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
