Securing a Higher Education Campus remains a significant challenge. There is a direct conflict between the open collaborative nature of our advanced institutes of learning and the perennial need to lock down all sources and targets of cyber threats. For example, in an EDUCAUSE survey, it identified cybersecurity as the number one IT issue for universities in 2024, reflecting the immense pressure on security teams.
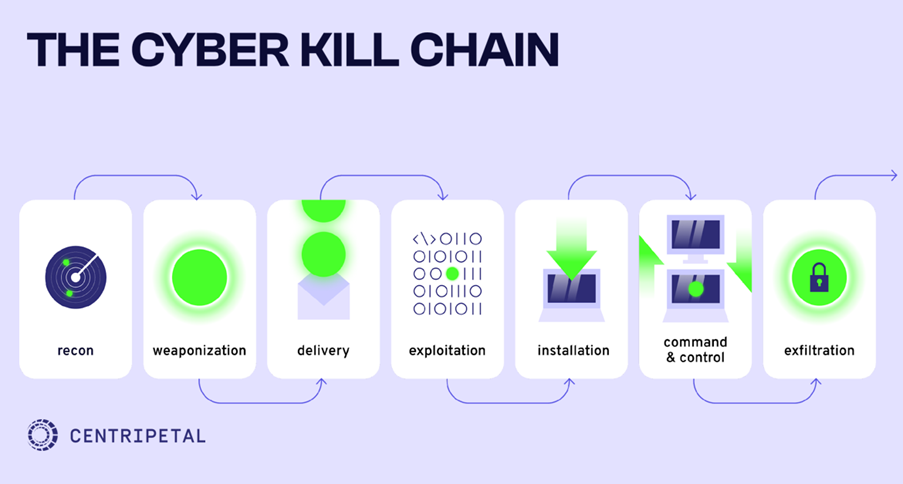
The Cyber Kill Chain outlines the typical stages of an infrastructure attack, from initial reconnaissance to the final execution of malicious objectives and provides insight into where proactive measures can be taken to reduce its impact. Traditional security tools such as Intrusion Detection Systems (IDS), Data Loss Prevention (DLP), and Endpoint Detection and Response (EDR) are designed to identify and flag anomalous behavior deep within the network.
However, due to the rapid spread of cyber threats in a campus environment, these tools often detect security incidents only after an attack has already occurred. By the time an alert is generated, malware may have already established a foothold, making mitigation significantly more challenging.
Focusing effort on the early stages of the kill chain – specifically reconnaissance and initial access – is a preferred approach to preventing breaches in a campus network. This is referred to by Gartner and others as a ‘Shift Left’ approach. The detect and respond approach is inadequate in today’s fast moving threat environment. By leveraging threat intelligence at scale, it is possible to screen every packet of data entering or leaving the network, identifying traffic to or from known malicious domains. Such an approach enables the eradication of reconnaissance traffic, and most of the threat traffic found in a typical campus network.
Centripetal does this for many large educational institutions around the world. By adopting this ‘Shift Left’ approach, higher level education organizations can reduce their security exposure significantly without incurring significant cost.
Centripetal enables higher education institutions and universities to proactively mitigate cyber threats at the earliest possible stages of the Cyber Kill Chain, reducing risk exposure before attacks can escalate. Traditional cybersecurity approaches often focus on reactive detection and response at later stages such as Exploitation, Installation, and Command & Control. However, our Shift Left approach emphasizes pre-emptive threat intelligence, predictive analytics, and automated enforcement, allowing universities to stop threats before they materialize into breaches.
By applying advanced threat intelligence-driven security, Centripetal ensures that malicious reconnaissance activities are neutralized, preventing adversaries from gathering valuable information about institutional networks. Our automated enforcement mechanisms block known threat actors prior to the Delivery and Exploitation phases, significantly reducing the attack surface, without placing additional operational burden on university security teams.
This proactive security model helps higher education organizations enhance their cyber resilience, ensuring compliance with data protection regulations (GDPR, FERPA, etc.) while reducing the cost and complexity of traditional security operations. By integrating our Shift Left strategy with existing security frameworks, universities can focus their resources on innovation and research, rather than constantly firefighting cyber threats.
Learn more about how Centripetal can protect your higher education institution with a shift left strategy today.
